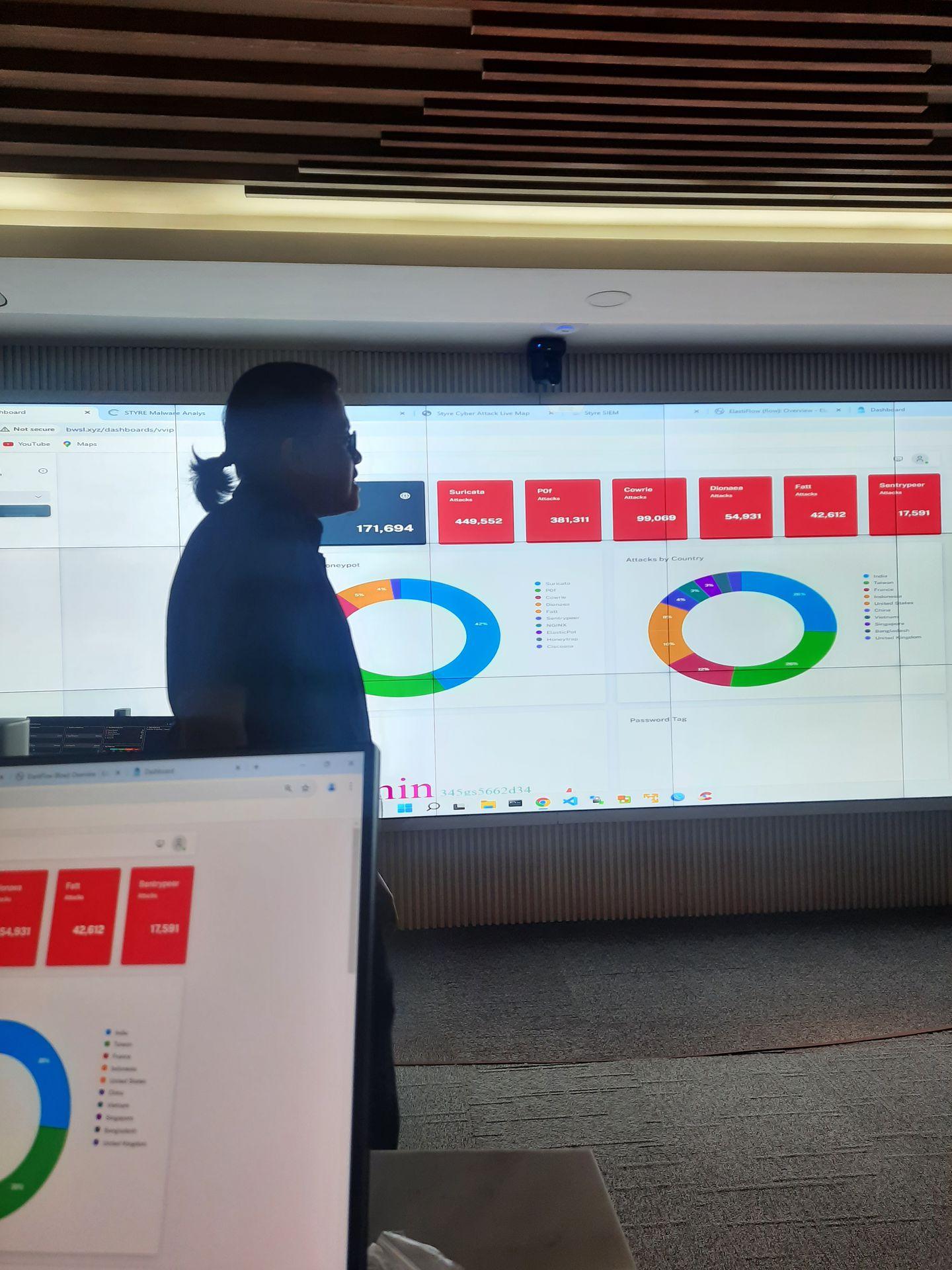
Introduction
STYRE Cyber Threat Intelligence (CTI) is designed to enhance an organization's ability to detect, understand, and respond to digital threats, particularly malware and spyware. Its primary goal is to provide both strategic and tactical information that helps organizations better comprehend the evolving threat landscape and strengthen their defenses accordingly. STYRE CTI enables early detection of threats by identifying patterns and indicators of ongoing or emerging attacks, allowing for faster and more effective responses. It also offers insights into the type and origin of threats, such as those coming from specific hacker groups or nation-state actors, and classifies them by nature, including ransomware and keyloggers. By delivering up-to-date intelligence on the latest techniques used by threat actors, STYRE CTI raises security awareness and helps teams stay informed. Furthermore, it provides deeper context behind threats—such as attacker motivations, objectives, and the tactics, techniques, and procedures (TTPs) employed—empowering organizations to proactively defend their networks and minimize the impact of cyberattacks.
Requirement
-
The system must integrate SOAR, XDR, and SIEM technologies into a single unified platform.
-
It should be capable of real-time threat detection from various data sources.
-
Provide automated incident response based on predefined playbooks.
-
Have a centralized incident management dashboard for monitoring, documentation, and handling.
-
Offer reporting and audit trail features for tracking and security audit purposes.
-
Maintain a minimum uptime of 99.9% to ensure service availability.
Result
The objective is to serve as a Monitoring and Incident Response System for Data Security. This testing plan provides the necessary approach to validate that each process functions correctly and that the system requirements have been met. It outlines the approach and strategy for solution testing, explains the planning, preparation, and scheduling of test cases including resource requirements, describes the execution, documentation of results, and test reviews, and provides the test cases to be executed for this testing effort. The purpose of this report is to detail the steps taken in the implementation of the Monitoring and Incident Response System for Data Security with Styre Threat Intelligence, as well as the online training. This report aims to assist the client in monitoring the status and progress of the work performed and evaluating whether the project is proceeding according to the agreed plan.